Step 1: Verify Prerequisites for Linux Installation
System Requirements- We recommend installing Skedler Alerts in a separate VM or Docker container or server.
- Linux Operating System with x86 64-bit architecture
- Ubuntu version 12.04 and above
- Debian version 7 and above
- Minimum of 2 CPU cores and 8 GB of RAM is recommended for deploying Skedler Alerts
- If you are using Skedler Alerts 3.1 version or earlier, please create alerts with a new index (or) deleting the existing alert's index.
Library Dependencies
- Ubuntu version 12.04 and above
- Debian version 7 and above
libnss3 library
- Debian/Ubuntu – sudo apt-get install libnss3
- CentOS/RedHat – sudo yum install libnss3.so libnssutil3.
1. Check hostname by giving this command:
$hostname
In alertConfig.yml the host parameter is the host in which Skedler Alerts binds.
2. If the host is configured as 127.0.0.1 then make sure you have an entry in /etc/hosts as mentioned below,
127.0.0.1 localhost
Note: If you are binding Skedler Alerts to the localhost you can't access it from outside.
3. However, if the bind-address is 0.0.0.0 in alertconfig.yml then Skedler Alerts binds to any IP (configured for your system). In this case, your entry in the hosts' file(/etc/hosts) should be
<ipaddress> <hostname>
4. If the host(IP address of the server) in alertConfig.yml is changed other than the default value 0.0.0.0 then there should be an entry for the host in /etc. hosts like
<ipaddress> <hostname>
5. Reboot the system.
Note: If you are using any proxy server add your hostname to a no_proxy list in the file /etc/environment add the following line,
no_proxy="<ipaddress>,<hostname>"
Elasticsearch version
Skedler Alerts supports the Elasticsearch version from 5.x to 7.11.xStep 2: Download
- Download the latest version of Skedler Alerts from the Download page.
Step 3: Extract
- Extract the skedler-alerts.tar.gz file to the desired folder (e.g., /opt). For convenience, let us call this folder as $alert_home.
Step 4: Install Skedler Alerts
- Provide the required permission to install.sh in $alert home script file using the command
- cd $alert_home
- sudo chmod u+x install.sh
- Install Skedler Alerts using the below command. Run install.sh as sudo user
sudo ./install.sh
Step 5: Configure alertconfig.yml
- Go to config folder using the command cd config.
- Open alertconfig.yml (e.g., vi /opt/alert/config/alertconfig.yml)
ElasticSearch URL configuration
Add Elasticsearch URL with the port (even if the port is 80) in the alertconfig.yml file in the following format

Security Configuration
For Skedler Alerts to connect with Elasticsearch Security you would need to configure the following properties in the Security Settings section in alertconfig.yml.
- By default, the security variable is commented and set to x-pack. If any security plugin for Elasticsearch such as X-pack or Search Guard or ReadOnlyRest or Open Distro is configured, uncomment the variable and configure the variable security with the respective value given below:
- For Xpack configure the security variable as x-pack
- For Search Guard configure the security variable as searchguard
- For ReadOnlyRest configure the security variable as readonlyrest
- For Open Distro configure the security variable as the open distro

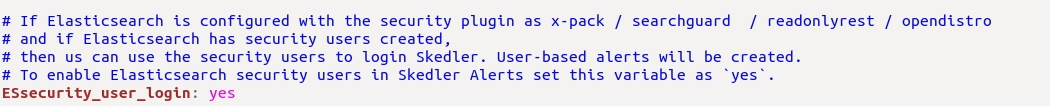
- If Elasticsearch is configured with the security plugin, and if Elasticsearch has security users created then you can use the security users to login Skedler Alerts. To enable Elasticsearch security users in Skedler Alerts set the ESsecurity_user_login variable as yes. By default, the variable is set to no.
- For Skedler Alerts to access Elasticsearch, set the security username and password created for Skedler Alerts.

Proxy server basic authentication configuration
- If you are using Nginx, follow the steps below.
If Nginx is configured as a reverse proxy for Elasticsearch, configure Nginx username and password for Elasticsearch as shown:

- Note: If you are using Shield then refer to Step-by-Step Configuration Guide for Shield.
- Save changes to alertconfig.yml
For more configuration options please refer alertconfig.yml configuration.
Step 6: Start Skedler Alerts
You can start Skedler Alerts as a service or manually.
- To start Skedler Alerts as a service, execute
sudo service alert start
- To start Skedler Alerts manually
Change directory to $alert_home (e.g., /opt/alert) and execute
bin/alert
Step 7: Access Skedler Alerts
Skedler Alerts can be accessed from the following URL http://<yourServer>:3001.
Step 8: Schedule Skedler Alerts
To configure Skedler Alerts settings, refer to How to configure time zone settings, index pattern settings, email settings, Webhook settings for skedler alerts
Step 2: Download
- Download the latest version of Skedler Alerts from the Download page.
Step 3: Extract
- Extract the skedler-alerts.tar.gz file to the desired folder (e.g., /opt). For convenience, let us call this folder as $alert_home.
Step 4: Install Skedler Alerts
- Provide the required permission to install.sh in $alert home script file using the command
- cd $alert_home
- sudo chmod u+x install.sh
- Install Skedler Alerts using the below command. Run install.sh as sudo user
sudo ./install.sh
Step 5: Configure alertconfig.yml
- Go to config folder using the command cd config.
- Open alertconfig.yml (e.g., vi /opt/alert/config/alertconfig.yml)
ElasticSearch URL configuration
Add Elasticsearch URL with the port (even if the port is 80) in the alertconfig.yml file in the following format

Security Configuration
For Skedler Alerts to connect with Elasticsearch Security you would need to configure the following properties in the Security Settings section in alertconfig.yml.
- By default, the security variable is commented and set to x-pack. If any security plugin for Elasticsearch such as X-pack or Search Guard or ReadOnlyRest or Open Distro is configured, uncomment the variable and configure the variable security with the respective value given below:
- For Xpack configure the security variable as x-pack
- For Search Guard configure the security variable as searchguard
- For ReadOnlyRest configure the security variable as readonlyrest
- For Open Distro configure the security variable as the open distro

- If Elasticsearch is configured with the security plugin, and if Elasticsearch has security users created then you can use the security users to login Skedler Alerts. To enable Elasticsearch security users in Skedler Alerts set the ESsecurity_user_login variable as yes. By default, the variable is set to no.

- For Skedler Alerts to access Elasticsearch, set the security username and password created for Skedler Alerts.

Proxy server basic authentication configuration
- If you are using Nginx, follow the steps below.
If Nginx is configured as a reverse proxy for Elasticsearch, configure Nginx username and password for Elasticsearch as shown:

- Note: If you are using Shield then refer to Step-by-Step Configuration Guide for Shield.
- Save changes to alertconfig.yml
Step 6: Start Skedler Alerts
You can start Skedler Alerts as a service or manually.- To start Skedler Alerts as a service, execute
sudo service alert start
- To start Skedler Alerts manually
Change directory to $alert_home (e.g., /opt/alert) and execute
Step 7: Access Skedler Alerts
Skedler Alerts can be accessed from the following URL http://<yourServer>:3001.
Step 8: Schedule Skedler Alerts
To configure Skedler Alerts settings, refer to How to configure time zone settings, index pattern settings, email settings, Webhook settings for skedler alerts
You are now ready to start scheduling Alerts.
Step 9: License Upgrade
Activation is required for the purchased product license key. In the Community Edition, license activation will be skipped. If you purchase a Skedler Alerts license, you will receive a license key by email.
Refer to Upgrade License
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article